Secure SSH Login For IoT & Download Guide!
Is the ability to securely access and manage Internet of Things (IoT) devices a critical component of modern infrastructure? The proliferation of interconnected devices demands robust and reliable methods for remote access, data transfer, and software updates, making SSH login and IoT download capabilities paramount to their effective operation and security.
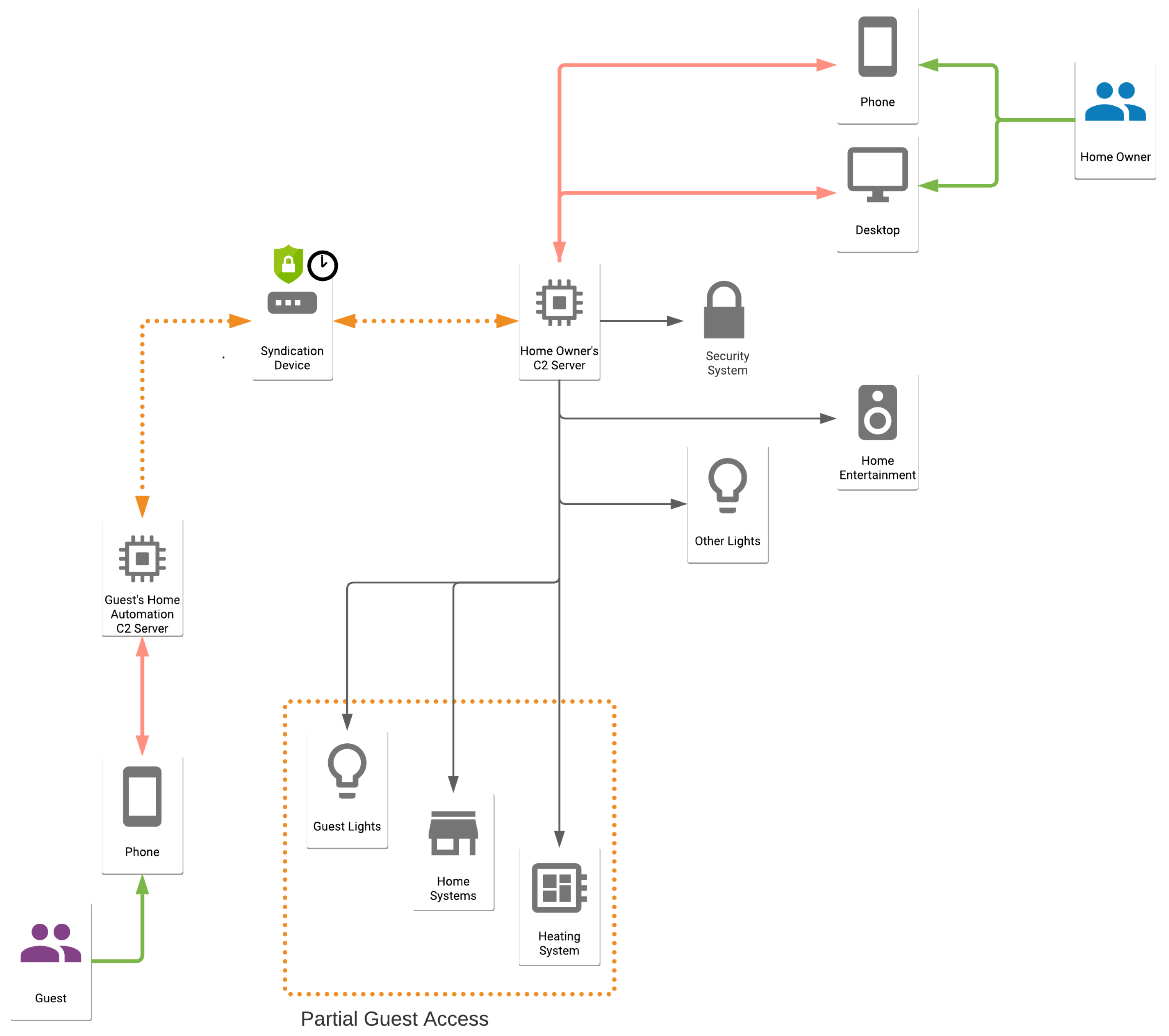
The intersection of Secure Shell (SSH) login and IoT device management has become a pivotal area of focus for developers, IT professionals, and security experts alike. SSH, a cryptographic network protocol, provides a secure channel for accessing a remote machine, enabling the execution of commands, file transfer, and the establishment of secure tunnels. In the context of IoT, where devices are often deployed in remote and potentially vulnerable locations, SSH offers a vital layer of protection. The ability to securely "ssh login" is not just a convenience; it's a fundamental requirement for maintaining control, troubleshooting issues, and deploying updates to a vast and geographically dispersed network of devices. The "iot download" aspect extends this functionality, allowing for the seamless transfer of software, configuration files, and other essential data to the IoT devices, ensuring they remain up-to-date and functional. The integration of these two concepts, therefore, represents a cornerstone of modern IoT security and operational efficiency, and understanding their interplay is essential for anyone working with these devices.
| Category | Details |
|---|---|
| Concept | SSH Login and IoT Download |
| Definition | Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. SSH login allows for remote access to devices, and IoT download refers to the process of transferring files to IoT devices. |
| Importance in IoT | Provides secure remote access, facilitates software updates, enables configuration management, and enhances overall device security and operational efficiency. |
| Key Features of SSH | Authentication (password, key-based), encryption, command execution, file transfer (using protocols like SCP or SFTP), and port forwarding. |
| IoT Download Mechanisms | Over-the-Air (OTA) updates, firmware updates, configuration file updates, and application deployment. |
| Security Considerations | Strong passwords or key-based authentication, regular security audits, firewall configuration, and monitoring of SSH login attempts are crucial for maintaining a secure IoT environment. |
| Best Practices | Disable password authentication, use SSH keys, limit SSH access to specific users, monitor SSH logs, and keep SSH software updated. |
| Tools and Technologies | OpenSSH, PuTTY (for Windows), SCP, SFTP, and specialized IoT management platforms. |
| Challenges | Securing diverse IoT devices, managing large-scale deployments, handling resource constraints on devices, and mitigating against evolving cyber threats. |
| Future Trends | Increased automation, integration of machine learning for anomaly detection, enhanced security protocols, and improved device management platforms. |
| Example Use Cases | Smart home devices (security cameras, smart locks), industrial automation (sensors, controllers), and connected vehicles. |
| Regulatory Compliance | Adherence to data privacy regulations (e.g., GDPR), industry-specific security standards, and ensuring the security and integrity of data transmitted and stored by IoT devices. |
| Resource Constraints | Addressing the computational limitations of IoT devices, such as memory, processing power, and battery life, while implementing robust security protocols. |
| Automation and Scripting | Automating SSH login and IoT download tasks using scripting languages (e.g., Bash, Python) to streamline device management and reduce manual effort. |
| Network Segmentation | Implementing network segmentation to isolate IoT devices from the main network, thereby limiting the impact of potential security breaches and restricting lateral movement. |
| Link to Website | Example IoT Security Resource |
The implementation of SSH login for IoT devices typically involves configuring the SSH server on the device itself. This can be achieved using various methods, depending on the operating system of the device and the available resources. For devices running Linux-based systems, OpenSSH is the most commonly used implementation. The configuration involves ensuring the SSH server is enabled, setting up user accounts with appropriate permissions, and, crucially, securing the login process. This often includes disabling password-based authentication in favor of key-based authentication, which is significantly more secure. Key-based authentication utilizes cryptographic keys to verify the identity of the user, eliminating the risk of password brute-force attacks. Furthermore, it's vital to change the default SSH port (port 22) to a less common port to reduce the likelihood of automated attacks. Regular monitoring of SSH logs is also essential to detect any suspicious activity, such as failed login attempts or unauthorized access. For IoT devices with limited resources, it might be necessary to optimize the SSH configuration to minimize the impact on performance, such as disabling unnecessary features or using a lightweight SSH implementation.
The "iot download" process encompasses various methods for transferring data to IoT devices. Over-the-Air (OTA) updates are a prevalent technique, especially for firmware updates. This allows for the seamless and remote deployment of software updates to a fleet of devices, without requiring physical access. OTA updates are essential for maintaining device security, fixing bugs, and adding new features. The process typically involves uploading the new firmware to a central server and then initiating the update process on the devices. Secure communication channels, such as HTTPS, are often employed to ensure the integrity and confidentiality of the update process. Configuration file updates are another critical aspect, where devices receive updated settings and parameters to adapt to changing operational environments. This could involve changing network settings, updating security credentials, or modifying device behavior. Application deployment is also vital, enabling the installation and updating of software applications on the devices. This is particularly important for IoT devices that support complex functionalities and require ongoing software maintenance. The security considerations for IoT downloads are significant and include verifying the authenticity and integrity of the downloaded files using digital signatures, ensuring secure communication channels, and implementing mechanisms to prevent unauthorized access or modification of the update process. Implementing these safeguards is crucial to prevent malware injection and ensure the devices operate as intended.
The importance of securing SSH login and IoT download capabilities extends beyond the basic functionality of the devices. It significantly impacts overall network security. If an IoT device is compromised through a weak SSH configuration or a vulnerability in the download process, it can serve as a gateway for attackers to access the broader network. This highlights the importance of implementing a defense-in-depth approach, which incorporates multiple layers of security. Network segmentation, for instance, isolates IoT devices from the main network, limiting the impact of a potential breach. Intrusion detection systems (IDS) and intrusion prevention systems (IPS) can monitor network traffic for malicious activity and automatically take action to mitigate threats. Regular security audits and penetration testing are vital to identify vulnerabilities and proactively address potential weaknesses. Furthermore, the rapid evolution of cyber threats necessitates ongoing monitoring and adaptation of security measures. This includes staying informed about the latest vulnerabilities, patching software promptly, and updating security configurations regularly.
One of the challenges in implementing secure SSH login and IoT download capabilities is managing the diverse range of IoT devices. IoT ecosystems are characterized by a wide variety of devices, each with its own operating system, hardware constraints, and security requirements. Developing a unified approach to security that caters to all devices can be complex. Another challenge is the resource constraints of many IoT devices. These devices often have limited processing power, memory, and battery life. Implementing complex security protocols can impact performance and battery life, which can be a significant issue for devices in remote locations. Managing a large-scale deployment of IoT devices also presents its own set of challenges. When dealing with thousands or even millions of devices, it becomes essential to have automated management tools to efficiently deploy updates, monitor devices, and respond to security incidents. These tools should provide centralized control, comprehensive logging, and real-time monitoring capabilities. The security landscape continues to evolve. This constantly changing environment necessitates vigilance and proactive measures to protect IoT devices from new and emerging threats. This includes staying abreast of the latest security research, participating in industry forums, and collaborating with security experts to share knowledge and best practices. The cost-effectiveness of deploying and maintaining secure SSH and IoT download capabilities is another critical consideration. While security measures are essential, organizations must balance the costs of implementation and maintenance with the potential risks. This involves carefully evaluating the return on investment (ROI) of different security measures and prioritizing those that provide the greatest value.
In the realm of practical applications, the combined use of SSH login and IoT download is evident across various sectors. In smart homes, for instance, SSH login allows for the secure remote management of devices like security cameras, smart locks, and thermostats. This enables homeowners to remotely monitor their property, control access, and update device firmware. The "iot download" capability ensures that these devices receive the latest security patches and feature updates, enhancing their overall security and functionality. In industrial automation, SSH login is often used to remotely access and manage industrial control systems (ICS). This enables technicians to diagnose and resolve issues, update software, and monitor the performance of critical infrastructure. The ability to securely download firmware updates is essential for ensuring the reliable operation of these systems. In the automotive industry, SSH login is used to access and manage the embedded systems of connected vehicles. This includes the ability to remotely diagnose issues, update software, and manage the security of the vehicle's communication systems. The seamless transfer of software updates over the air is vital for maintaining the safety and performance of these vehicles. Furthermore, the emergence of edge computing is driving the need for secure SSH login and IoT download capabilities. Edge devices, which are located close to the data source, require robust security measures to protect sensitive data. SSH login and secure download mechanisms are crucial for remotely managing and updating these devices.
As the IoT landscape evolves, future trends are set to further shape the use of secure SSH login and IoT download. Automation is poised to play an increasingly significant role. Automation tools will streamline the management of large-scale deployments, enabling automatic updates, configuration changes, and security monitoring. Machine learning (ML) and artificial intelligence (AI) will also play an increasing role in the future of IoT security. ML and AI can be used to detect anomalies, identify threats, and automate incident response. Enhanced security protocols, such as the adoption of post-quantum cryptography, will be crucial to protect against the evolving threat landscape. IoT device management platforms will become more sophisticated, providing centralized control, comprehensive logging, and real-time monitoring capabilities. The integration of blockchain technology is also expected to influence the way IoT devices are managed and secured. Blockchain can be used to secure device identities, ensure the integrity of data, and create immutable audit trails. Furthermore, the increasing focus on data privacy regulations, such as GDPR, will drive the need for enhanced security measures. This includes the implementation of strong encryption, access controls, and data anonymization techniques. Standardization and interoperability will also be vital, as the proliferation of IoT devices increases the need for seamless integration and compatibility across different platforms and vendors. The evolving threat landscape necessitates continuous vigilance and adaptation. Staying informed about the latest vulnerabilities, patching software promptly, and updating security configurations are essential to protect IoT devices and ensure their secure operation. In conclusion, the future of SSH login and IoT download in the IoT domain is intrinsically tied to ensuring the security, efficiency, and manageability of these interconnected devices. The ongoing evolution of threats and the ever-expanding footprint of IoT demand constant vigilance and proactive measures to fortify these critical functionalities. The focus should be on building a comprehensive security strategy that adapts to the complex challenges of the digital landscape, encompassing the latest technological advancements and industry best practices.